



|
|
|
Image Secret Sharing-Based Selective
Encryption
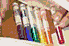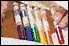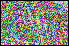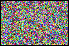 Operating
on the bit-levels of the secret image, encryption operations such as
image secret sharing-based encryption can be selectively performed
depending on the application constraints and/or user's needs. In this
way, the encryption process alters only the selected bits while the
remaining bits are kept unchanged. The figure on the left shows shares
obtained respectively using no encryption and by encrypting the third
most significant bit, the second most significant bit, the most
significant bit, and the three most significant bits of each color
component. The
confidentiality increases with the significance of bits being encrypted.
A sufficient level of protection of the visual information is achieved
by encrypting the first two or three most significant bits. Operating
on the bit-levels of the secret image, encryption operations such as
image secret sharing-based encryption can be selectively performed
depending on the application constraints and/or user's needs. In this
way, the encryption process alters only the selected bits while the
remaining bits are kept unchanged. The figure on the left shows shares
obtained respectively using no encryption and by encrypting the third
most significant bit, the second most significant bit, the most
significant bit, and the three most significant bits of each color
component. The
confidentiality increases with the significance of bits being encrypted.
A sufficient level of protection of the visual information is achieved
by encrypting the first two or three most significant bits.
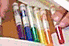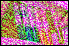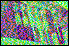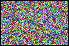 Another important factor in color image encryption is the
color information. The figure on the right depicts share images
generated when
the encryption operations are selectively applied to the particular
color channels. Images correspond respectively to no encryption,
and the encrypted red, green, blue, red+green, red+blue, green+blue, and
red+green+blue channels. As it can be seen from the presented example, encrypting either one or two color channels
does not completely obscure the actual input. This suggests that for
secure image secret sharing-based encryption, all the channels of the
color RGB image should be encrypted. Another important factor in color image encryption is the
color information. The figure on the right depicts share images
generated when
the encryption operations are selectively applied to the particular
color channels. Images correspond respectively to no encryption,
and the encrypted red, green, blue, red+green, red+blue, green+blue, and
red+green+blue channels. As it can be seen from the presented example, encrypting either one or two color channels
does not completely obscure the actual input. This suggests that for
secure image secret sharing-based encryption, all the channels of the
color RGB image should be encrypted.
|
|
References: |
|
 |
R. Lukac and K.N. Plataniotis, Secure Color Imaging. In Color
Image Processing: Methods and Applications, (eds.) R. Lukac and
K.N. Plataniotis, CRC Press / Taylor & Francis, pp. 185-202, October 2006. ISBN 0-8493-9774-X |
 | R. Lukac and K.N. Plataniotis, "A Cost-Effective Encryption Scheme for Color Images,"
Real-Time Imaging, Special Issue on Multi-Dimensional Image
Processing, vol. 11, no. 5-6, pp. 454-464, October-December 2005. |
|
|
|
